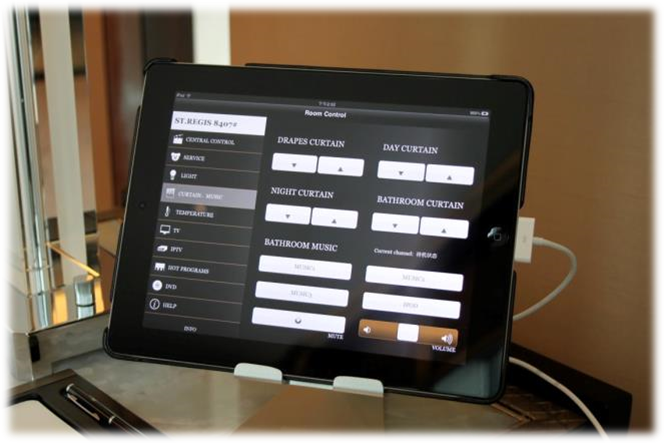
In December 2013 I was able to abuse the insecurity of the KNX/IP protocol in a large home automation setting: The St. Regis Hotel in ShenZhen. The KNX Association responded to the incident with a brief statement on their webpage. The response seems odd, as it is half an apology for being an old standard that failed to keep with the security requirements of a connected world, half defending their security because they provide security through obscurity (ironically, it is supposed to be an “open “standard”)
First, quoting the statement
The cradle of the KNX system lies as far back as the nineties, where security issues were not such a hot topic as they are today. In the recent years, KNX and its members have considerably invested in the improvement of the KNX Standard with data security mechanism, which has materialized in an updated KNX.
As discussed in my talk, since 2006 researchers pointed out the problem with a paper called EIBsec: a security extension to KNX/EIB. The new standards that added some mysterious security mechanisms appeared in 2013. To add insult to injury, all the security papers were previously hosted by the KNX association (dead link) - Google Scholar but since my talk they have disappeared mysteriously.
And that is my main problem with KNX: it is a closed, dated protocol, that follows non-transparent rules of operation and costs thousands of dollars just to download, preventing possible improvements by researchers. My suggestion for moving forward: add transparency, in particular if you want to declare yourself as an open standard. We live in 2014, not 1990. And to prove my point:
Also to be borne in mind is the fact that KNX runtime communication makes use of untyped information; this means that without the availability of the project data, address and data information can be seen, but cannot be interpreted. It is therefore not surprising that the researcher had to invest “a couple of days” to “figure out the codes” in the hotel installation. A “passer-by” would have a hard time achieving the same result.
And this statement suggests the we are secure because we are not transparent approach, which is exactly the problem I am referring to.
This is not the only building affected by poor security practices, and I point to the lack of transparency of the KNX association as the problem. Note that I tested other buildings and they are also susceptible to attacks.
Thank you very much to all of you that attended my talks at BlackHat and Defcon. If you are interested in the supporting materials of the talk, I am providing a local mirror for download:
I will publish the code in a couple of weeks (decode KNX payloads and address and send KNX/IP)
###Hotel Response### I want to thank the Starwood group for their support for the talk. As discussed in the NPR article To Hack or Not to Hack sometimes the actions of the affected parties after an intrusion is either timid or downright aggressive against the security researchers involved. Their reaction should serve as a template for other companies. Security researchers are here to serve the community and help to prevent real problems in the future, and the Hotel and their leadership demonstrated that their guests are the top priority and opened dialogue to find a solution. Notice the sharp contrast to the indifferent response by the KNX association.
This blog post is not a troll against OpenStack. It started as a response to a twitter post, and transitioned to a reflection on the governance of Open Source projects and its impact on the code. And I am not implying Openstack is worse than Linux, just that it is a different form of open source, is not the Linux for cloud and I will tell you why. Linux was created with a vision, to provide a free and open operating system while OpenStack is just a tool to pool resources between companies to create an open cloud ecosystem. This reflects in several aspects of OpenStack, but the more glaring difference is Governance.
OpenStack and CloudStack are open source software to create infrastructure as a service (IaaS) clouds. Both are under the Apache License, which allows creating derivative projects, and even close sourcing them as long as you maintain the copyright notices. They represent a new wave of open software, where companies open their code to pool resources to other interested parties (another relevant example of that trend is CloudFoundy to create PaaS). I recently attended the respective conferences for these software packages. More than the contents, the dynamics of each conference provided a very representative insight of the software.